The Shadowy World of Smartphone Spying: What’s Next for Predator and Beyond
Recent revelations about the Predator spyware, developed by the Israeli firm Intellexa, and its use against individuals in countries like Egypt and Saudi Arabia, have sent ripples through the cybersecurity world. Apple and Google have issued warnings, but the threat extends far beyond a single piece of software. This isn’t just about sophisticated hacking; it’s a glimpse into a rapidly evolving landscape of digital surveillance, and understanding its trajectory is crucial.
The Rise of ‘Mercenary Spyware’
Predator, often compared to the notorious Pegasus spyware, represents a new breed of surveillance tool. These aren’t the work of lone hackers; they’re commercially available, state-sponsored (or state-adjacent) technologies. Intellexa, despite US sanctions, continues to operate, selling its capabilities to governments and entities willing to pay a premium – reportedly up to $250,000 for a single target. This market for “mercenary spyware” is expanding, with companies vying to offer increasingly sophisticated intrusion methods.
Zero-Day Exploits: The Cost of Silence
A key component of Predator’s effectiveness lies in its exploitation of “zero-day” vulnerabilities – security flaws unknown to the software vendor and, therefore, unpatched. Intellexa reportedly purchases these vulnerabilities from hackers, effectively paying for the ability to bypass security measures. The cost of a zero-day exploit can range from $1 million to $3 million, depending on the target and potential impact. This creates a perverse incentive: the longer a vulnerability remains hidden, the more valuable it becomes to companies like Intellexa.
Beyond Predator: Emerging Trends in Mobile Hacking
While Predator is currently in the spotlight, several trends suggest the threat landscape will become even more complex. Here are some key areas to watch:
- AI-Powered Attacks: Artificial intelligence is already being used to automate vulnerability discovery and craft more convincing phishing attacks. Expect to see AI-driven malware that can adapt to security measures in real-time.
- Supply Chain Attacks: Targeting software supply chains – the process of developing and distributing software – is becoming increasingly common. Compromising a single component used by many applications can have a widespread impact.
- Clickless Exploits: Predator’s “Aladdin” capability, which allows attacks to be launched simply by displaying malicious advertisements, demonstrates a worrying trend. These “clickless” exploits require no user interaction, making them incredibly difficult to defend against.
- Expansion of Targets: Initially focused on journalists, activists, and political dissidents, the scope of surveillance is broadening. Businesses, lawyers, and even private individuals are now potential targets.
- The Proliferation of Nation-State Tools: Tools once exclusively used by governments are increasingly leaking into the hands of private companies and even criminal organizations.
The Role of 5G and IoT in Amplifying the Risk
The rollout of 5G networks and the proliferation of Internet of Things (IoT) devices are creating new attack surfaces. 5G’s increased speed and bandwidth enable faster data exfiltration, while the sheer number of insecure IoT devices – from smart home appliances to industrial sensors – provides attackers with countless entry points. A compromised smart thermostat, for example, could be used to gain access to a home network and, ultimately, to smartphones and computers.
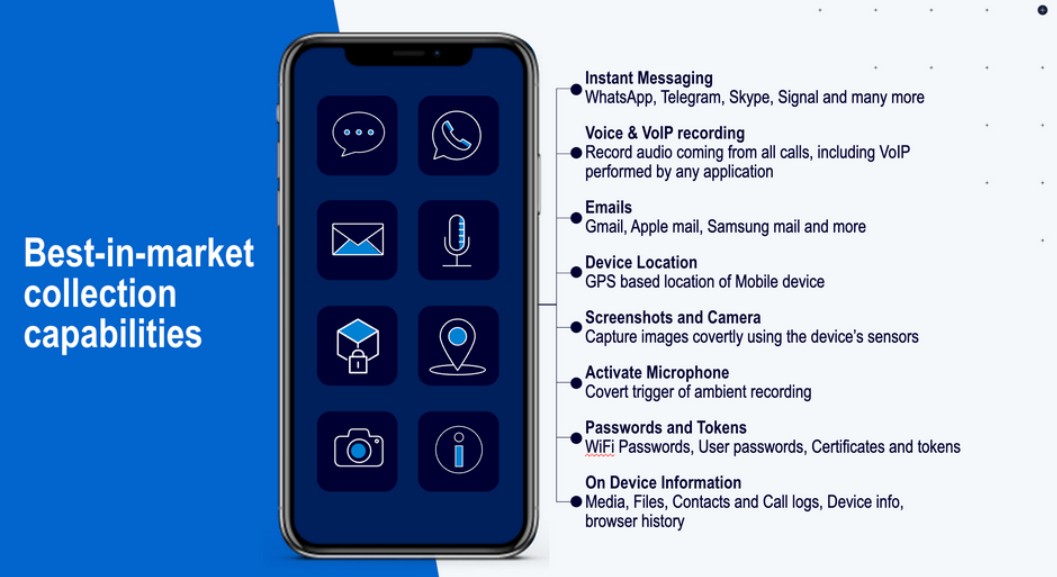
What Can You Do? Protecting Yourself in a Hostile Digital Environment
While complete protection is impossible, several steps can significantly reduce your risk:
- Keep Your Software Updated: Regularly update your operating system, apps, and security software. Patches often address critical vulnerabilities.
- Be Wary of Links and Attachments: Exercise extreme caution when clicking on links or opening attachments, especially from unknown senders.
- Use Strong Passwords and Two-Factor Authentication: Enable two-factor authentication wherever possible.
- Consider Using a VPN: A Virtual Private Network (VPN) can encrypt your internet traffic and mask your IP address.
- Review App Permissions: Regularly review the permissions granted to apps on your smartphone.
- Employ Endpoint Detection and Response (EDR) Solutions: For high-risk individuals, consider using EDR software that can detect and respond to advanced threats.
The Future of Digital Privacy: A Call for Regulation and Transparency
The rise of mercenary spyware highlights the urgent need for greater regulation and transparency in the cybersecurity industry. Governments must work together to establish clear rules governing the development, sale, and use of these technologies. Increased scrutiny of companies like Intellexa is essential, as is greater investment in research and development of privacy-enhancing technologies.

FAQ: Smartphone Spying and Your Privacy
- Q: Am I likely to be targeted by spyware?
A: Most individuals are not likely to be targeted. However, journalists, activists, political figures, and those involved in sensitive legal or business matters are at higher risk. - Q: Can antivirus software protect me from Predator?
A: Traditional antivirus software may not be effective against advanced spyware like Predator, which often employs sophisticated evasion techniques. EDR solutions offer a better level of protection. - Q: What is a zero-day exploit?
A: A zero-day exploit is a vulnerability in software that is unknown to the vendor and, therefore, unpatched. - Q: Is it possible to detect if my phone has been hacked?
A: Detecting spyware can be difficult. Signs may include unusual battery drain, increased data usage, or unexpected device behavior.
Pro Tip: Regularly review your phone’s security settings and be mindful of the apps you install. A little vigilance can go a long way.
What are your biggest concerns about digital privacy? Share your thoughts in the comments below, and explore our other articles on cybersecurity for more insights.

