The Rise of Voice Phishing: How Hackers Are Exploiting Trust to Breach Corporate Networks
A chilling new trend is sweeping across the cybersecurity landscape: voice phishing, or “vishing,” attacks targeting single sign-on (SSO) accounts. The notorious ShinyHunters extortion gang has claimed responsibility for a recent wave of these attacks, impacting major platforms like Okta, Microsoft, and Google. This isn’t just about stolen passwords; it’s about gaining a master key to entire corporate ecosystems.
How Vishing Works: A Deceptive Playbook
Unlike traditional phishing emails, vishing attacks leverage the power of human interaction. Threat actors impersonate IT support staff, contacting employees directly by phone. They use social engineering – manipulating individuals into divulging sensitive information – to trick victims into entering their credentials and multi-factor authentication (MFA) codes on convincingly crafted phishing websites. These sites perfectly mimic legitimate login portals, making it incredibly difficult for even tech-savvy users to detect the deception.
Once an SSO account is compromised, attackers gain access to a treasure trove of connected applications. Think Salesforce, Microsoft 365, Google Workspace, Slack, and countless others. A single successful vishing attack can unlock access to critical company data, intellectual property, and customer information.
Source: Microsoft
The ShinyHunters Connection and the Salesforce Focus
ShinyHunters, a well-known cybercrime group, has a history of data breaches and extortion. Their recent claim of responsibility for these vishing attacks is particularly concerning. They’ve specifically highlighted Salesforce as a primary target, suggesting they’re leveraging previously stolen data – including phone numbers and employee details from past Salesforce breaches – to make their social engineering attempts more convincing.
Did you know? ShinyHunters often targets companies with large customer databases, making them attractive targets for data theft and subsequent extortion.
The Evolution of Phishing Kits: Real-Time Manipulation
What makes these vishing attacks particularly sophisticated is the technology behind them. Okta’s recent report details phishing kits that allow attackers to dynamically alter the phishing website in real-time, based on the conversation they’re having with the victim. This means they can display specific prompts for MFA codes, push notifications, or other authentication steps, guiding the victim through the entire process. It’s a level of interactivity that significantly increases the success rate of these attacks.
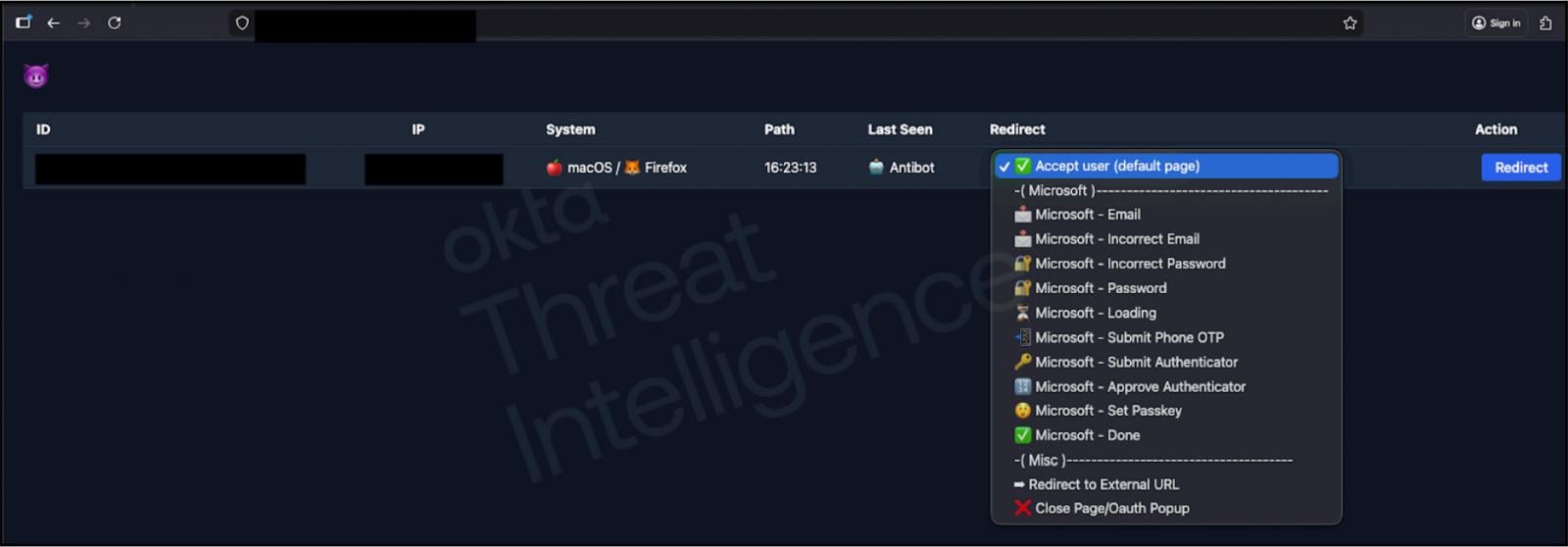
Source: Okta
Future Trends: What to Expect in the Coming Months
The rise of vishing attacks signals a broader shift in cybercriminal tactics. Here’s what we can anticipate:
- Increased Sophistication of AI-Powered Social Engineering: Expect to see attackers leveraging AI to generate more convincing scripts, mimic voices, and personalize attacks based on publicly available information.
- Expansion Beyond SSO: While SSO is a prime target now, attackers will likely expand their focus to other critical systems accessible via phone support, such as financial institutions and healthcare providers.
- More Targeted Attacks: Attackers will continue to refine their targeting, focusing on employees with high-level access and critical data.
- Rise of “Deepfake” Voice Cloning: The potential for attackers to clone the voices of trusted colleagues or superiors is a terrifying prospect that will likely become a reality.
- Focus on Bypassing MFA: As MFA becomes more widespread, attackers will invest more resources in techniques to bypass or circumvent it, including real-time phishing and SIM swapping.
Protecting Your Organization: A Proactive Approach
Combating vishing requires a multi-layered security strategy:
- Employee Training: Regularly train employees to recognize and report suspicious phone calls. Emphasize the importance of verifying the caller’s identity through independent channels.
- Strong MFA Policies: Implement strong MFA policies and encourage employees to use authenticator apps instead of SMS-based codes.
- Zero Trust Architecture: Adopt a zero-trust security model, which assumes that no user or device is inherently trustworthy.
- Incident Response Plan: Develop and regularly test an incident response plan specifically tailored to vishing attacks.
- Threat Intelligence Sharing: Share threat intelligence with industry peers to stay ahead of emerging threats.
Pro Tip: Encourage employees to be skeptical of any unsolicited phone calls requesting sensitive information, even if the caller appears to be legitimate.
The Role of AI in Defense
While AI is being used by attackers, it also offers powerful defensive capabilities. AI-powered security tools can analyze call patterns, detect anomalies, and identify potential vishing attempts in real-time. These tools can also automate threat detection and response, freeing up security teams to focus on more complex threats.
FAQ: Vishing Attacks – Your Questions Answered
Q: What is the biggest risk of a successful vishing attack?
A: Data breach, financial loss, reputational damage, and potential legal liabilities.
Q: Can MFA protect against vishing?
A: MFA significantly reduces the risk, but it’s not foolproof. Attackers can still trick victims into approving MFA requests in real-time.
Q: What should I do if I receive a suspicious phone call?
A: Hang up immediately and report the call to your IT security team.
Q: Are smaller businesses at risk?
A: Absolutely. Attackers often target smaller businesses because they typically have fewer security resources.
The threat of vishing is real and evolving. By understanding the tactics used by attackers and implementing proactive security measures, organizations can significantly reduce their risk of falling victim to these deceptive attacks. Staying informed and vigilant is crucial in this ever-changing threat landscape.
Explore more articles on cybersecurity best practices here. Subscribe to our newsletter for the latest threat intelligence and security updates.

